Passwords are the main means used by any user to authenticate in any service or system. However, the problem with passwords is that people usually tend to forget them a lot. In this case, they usually consult IT specialists or computer engineers who crack these passwords using various hashing algorithms. And you will know some knowledge about your computer: hash format are modern windows login passwords stored in. But for the sake of convenience, this article also offers a Windows password recovery tool: UnlockGo – Windows Password Recovery, you can crack the computer password at home without bothering others. Let’s dive in!
What Hash Format does Windows Use for Login Passwords?
For Windows operating systems, the hash of the passwords of the users of each machine is found in the SAM (Security Account Manager) file and depending on the version of the operating system, one of two algorithms is used: LM or NTLM.
LM (Lan Manager) encryption is a weak algorithm because of the way it is designed since, for example, it splits the password into two blocks of 7 bytes, converts all characters to uppercase and pads unused bytes with zeros; all of this facilitates a brute force attack. When it was replaced by NTLM (NTLan Manager), these errors were corrected, but even so, many systems for compatibility continue to store passwords in both formats, which is a clear security flaw.
So, in short, the answer to the question: What hash format are Windows passwords stored in” is an NT hash system.
How to Crack Windows Login Password with Hash
On Windows, the password is normally stored in the SAM file at %SystemRoot%\System32\config. Windows uses the NTLM hash; during boot time, the SAM file hashes are decrypted using SYSKEY, and the hashes are loaded into the registry, which is then used for authentication purposes.
Windows do not allow users to copy the SAM file to another location, so you have to use another operating system to mount the Windows system on top of it and copy the SAM file. Once the file is copied, we will decrypt the SAM file with SYSKEY and get the hashes to crack the password.
Note: This method is difficult and time-consuming for common computer user to crack Windows password, so this way is the perfect choice for you to disable windows password with ease.
Extracting Windows Password Hashes Using Cain
- First, download and install the famous Cain and Abel software by visiting the link Download Cain.
- In the next step, select “Run as Administrator” and open Cain for the first time.
- In Cain, click the Cracker icon from the upper set of tabs.
- Now by clicking in the right window, select ‘add to list’ as shown below.
- In the left section “Add NT Hashes from” box, accept the default selection of the system and “Import Hashes from the local system”, as shown below, and select ‘Next’.
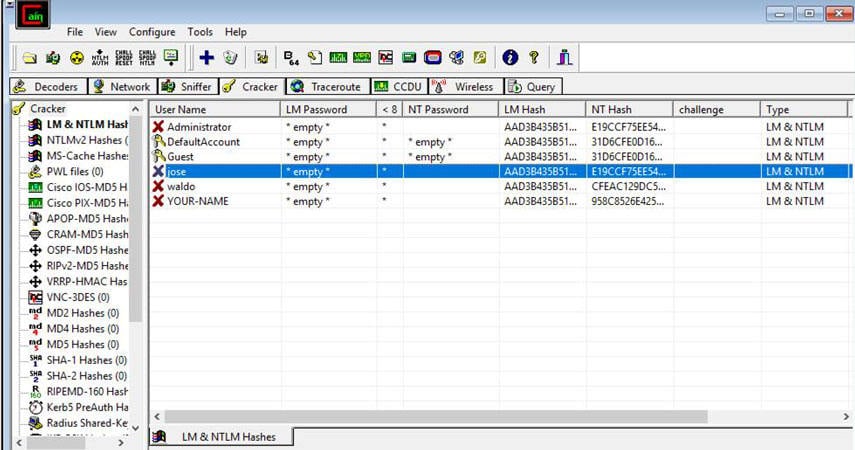
- The retrieved password hashes appear, as shown below.
Cracking Windows Password with Acquired Hash Using Ophcrack
The NTLM technique stores the hash in the MD4 algorithm, which can easily be cracked by the hackers, the above diagram shows the encrypted hash by Cain, and we will be using Ophcrack (A recovery tool) to crack the acquired Md4 hash.
Now, as we have acquired the hash, here comes the next step of choosing the best and fastest tool to crack the windows password hash.
- On your computer, visit the Ophcrack website and download Ophcrack LiveCD, which is compatible with Windows 10. The downloaded file will be in ISO format.
- After downloading the Ophcrack LiveCD, you will need to burn the ISO file to a CD or flash drive.
- From there, you can insert the bootable media into the computer to reset the computer. You will then see a screen like this.
- The Ophrcrack LiveCD menu should now appear. Please be patient while the computer loads this menu. However, you can still press the Enter button while still in the Ophcrack Graphic mode – auto menu.
- Once the menu has loaded, you will see a command line appear on the screen. Here Again, you don’t have to do anything but wait, as those are just commands that show Ophcrack LiveCD software is loading which will allow you to crack Windows 10 password.
- Then a window will appear shortly confirming the content of the encrypted password that is in the device that was inserted into the computer.
- The program will retrieve the administrator password and display it in the window. Click through the list and view the administrator account password.
- After making a note of the password, you can now log into your computer.


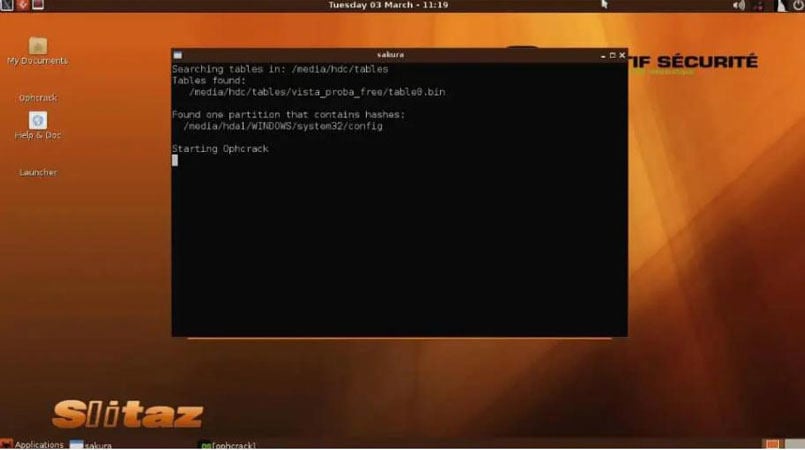
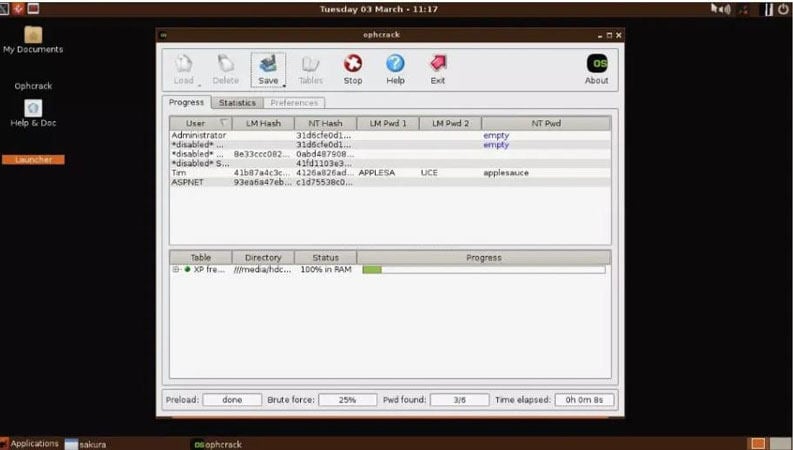
Ophcrack uses the famous Brute Force dictionary attack technique to crack windows password hash. Brute forcing is the most effective algorithm among all the hashing algorithms for windows. It works on Dump and Loads to utilize the real-time graphs for analyzing the windows password hash.
How to Crack Windows Login Password with Hash Alternative (Time-saving and Easy)
Cracking Windows passwords is not an easy task, and sometimes it would surely take too much time. Individuals working in offices and different sectors might sometimes lose their passwords and end up losing access to your Windows. This situation might be so hectic, but now no need to be worried, UnlockGo – Windows Password Recovery will surely help you to set out the new password for your windows without remembering the old one within a few clicks and minutes.
Just follow the below steps, and you can easily crack your windows password:
🔔 Step 1: First, install UnlockGo windows password recovery on your PC.
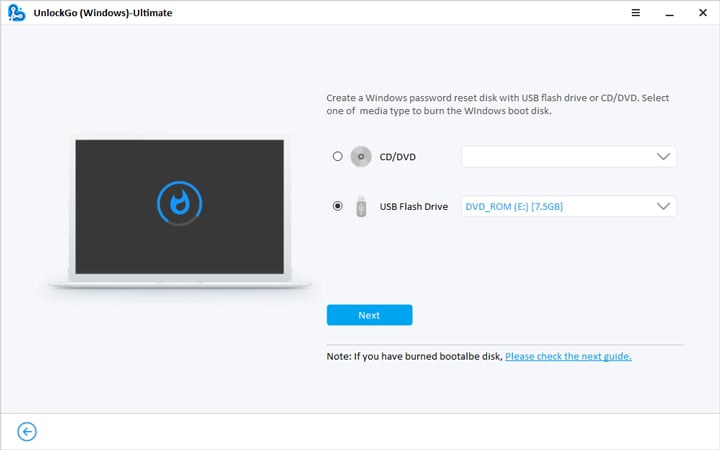
- 🔔 Step 2: Create a Windows password reset CD/DVD or USB, whatever is available.
- 🔔 Step 3: Now, after the bootable USB drive is ready, with UnlockGo, you have the option to reset or crack your windows password, delete the password or create a new account for the windows.
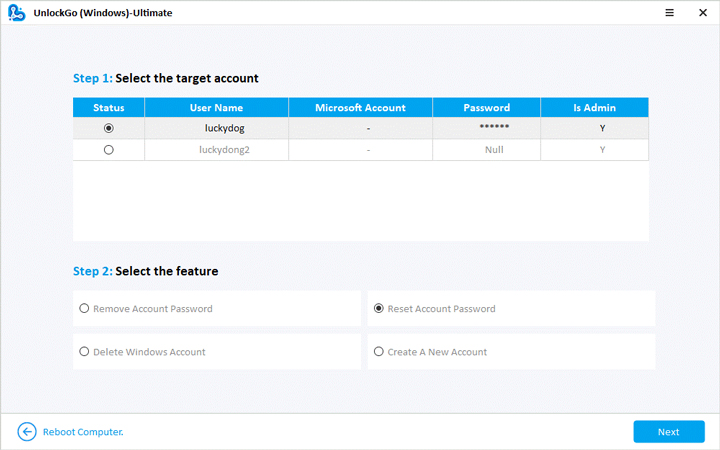
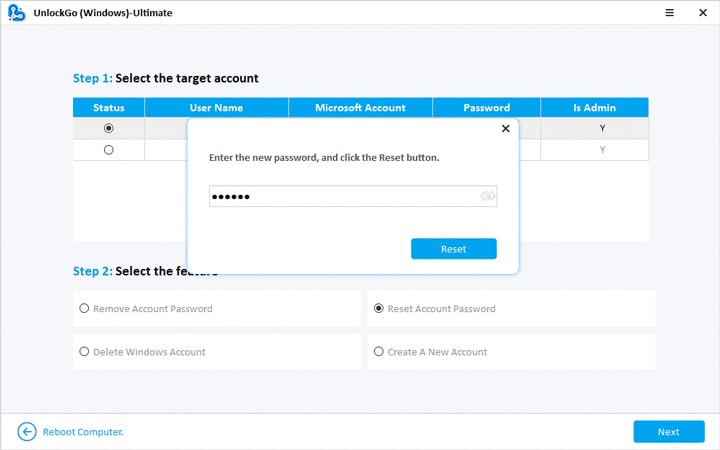
- 🔔 Step 4: Select the reset password option, and you are now all set to regain access to your computer.
FAQs about Windows Password Hash Format
❓ 1. How to acquire password hashes?
There are different ways to acquire password hashes:
Acquisition from the Machine In-Question
Although Windows password hashes are stored in the SAM file, their encryption is within the system boot key stored in the SYSTEM file. Both of these files are stored in C: WindowsSystem32Config. If someone accesses both of these files, then he can use the SYSTEM file for decrypting the passwords in the SAM file.
Using Authentication to a Remote Server
Taking the benefit of authentication to a remote server is another way of acquiring password hashes. This works by sending a user link pointing to a file on the hacker-controlled server in the form of a phishing email. This link can trick the target computer, which then tries to authenticate the activity with the current login credentials. Thus, stealing a password hash becomes possible by this method.
❓ 2. What password cracking tools, we can use?
There are different ways of cracking Windows passwords using different tools, such as Hashcat, John the Ripper, and Ophcrack.
Hashcat: It is a free, open-source password cracker for all DOS having GPU support.
John the Ripper: It is a password cracking tool. Its free version is available for all the Operating Systems, while its Pro version is available for *nix Operating Systems.
Ophcrack: It is yet another password cracking tool available for all operating systems.
❓ 3. How are Passwords Stored in Windows?
There are three ways the passwords are stored in Windows. These are:
Passwords being stored as OWF
OWF stands for One-way Function. It is a one-way method of mathematical transformation of data related to hashing algorithm for Windows. The data is transformed through this method and is converted only through one-way encryption, and this process cannot be reversed.
Passwords being Stored in Active Dictionary
The passwords at rest are secured in the Active Dictionary Database. The NT password hash gets protected by a dual encryption layer when stored in this form.
Passwords being Stored in Local SAM
A local Security Account Manager (SAM) is used for storing the local user account password hashes. The password hashes encrypted in SAM are done in the same way as the Active Dictionary.
Summary
Just like any piece of modern technology, Windows has also faced numerous updates with time. It has changed its interface and applications quite a lot. Also, its operability has been modified, but still, it is facing critical security issues. Windows needs to work on its hashing algorithm in the upcoming versions to ensure maximum security for its users; otherwise, the intruders and crackers might hack into windows easily. You can change them within months, and no worry about forgetting with our UnlockGo – Windows Password Recovery, feel free to encrypt your computer.

